While I know you’re excited to read ALL about data inventories, I’m most excited to tell you that I’ve been recording a training session all week in California. It’s something I’ve been working on for over a year, and I can’t wait to have it released soon!
Oh, and if you want to hear all about the super fascinating personal data mix-up that happened to me while renting a car, check out my social post that’s going bananas with people sharing their own crazy stories. Check it out!

So, I’m writing this after a long day of flying, jet lag, and recording … hopefully there aren’t TOO many typos!
Last week, I wrote about why no privacy program succeeds when it relies on a single person, and why having the right internal and external people is the foundation for everything else.
This week, I want to talk about the next layer: process, starting with one of the most important, most misunderstood, and most commonly avoided parts of privacy operations – the data inventory.
I’ve written a lot about data inventories over the years, and that’s because a data inventory is the FOUNDATION of any privacy program.
When an inventory is solid, privacy work becomes clearer, faster, and far more defensible.
When it’s missing, incomplete, or inaccurate, nearly every other privacy obligation becomes harder than it needs to be.
Oh, and GDPR requires one. Minnesota does too. CCPA’s regulations require businesses to assess data inventories as part of their cybersecurity audits.
And despite how central it is, many companies are in one of two situations:
- They don’t have a data inventory at all, or
- They have one, but it’s wrong, incomplete, or so disconnected from reality that no one fully trusts it.
The Two Ways Data Inventories Fail
Most data inventories fail in one of two ways.
First, many companies simply don’t have anything in place.
They may have a privacy notice, a cookie banner, or even a vendor review process, but if you ask, “How do you know what personal data you process, how you use it, and where it goes?” there isn’t a clear, organized answer.
Second, many inventories exist, but they’re wrong.
They miss systems, vendors, data uses, or categories of data that matter most—such as sensitive data, children’s data, or data used for AI. Or they’re written at such a high level that they can’t support real privacy work.
Once an inventory is wrong, teams stop relying on it, and at that point, it becomes a checkbox instead of a tool.
It’s why we always ask companies during our privacy program assessments whether they complete a data inventory AND to actually SEE their data inventory.
I’ve had plenty of companies proudly check the box that they are all set with their data inventory. Only to review it and see that it was just the one part of the product and nothing else, when it had oodles of other personal data, or it just covered a few IT systems and not how data was used, and a myriad of other stories.
Catch me at the next privacy conference, and I’ll share my many lacking data inventory tales.
Why This Happens So Often
Inaccuracy rarely comes from lack of effort. It usually comes from how inventories are built.
Many inventories are created:
- under intense time pressure
- with limited business participation
- by focusing on systems instead of behavior
- before privacy is embedded into everyday workflows
Which brings me to one of the most important distinctions I want to make.
Privacy Inventories Must Cover Processing Activities, Not Just Systems
From a privacy perspective, knowing which systems exist is not enough.
What matters most is understanding processing activities, which is documenting how personal data is actually:
- collected
- used
- stored
- shared or sold (credit to CCPA and copycat US laws)
- retained
This is why I’ve always loved GDPR’s concept of a Record of Processing Activities (ROPA). Yes, I just said love, GDPR and ROPA in the same sentence.
A ROPA forces companies to document how data flows through the business, not just where it sits technically. It captures the reality of how data is handled, why it’s handled that way, and what risks are created along the way.
Too many data inventories originate with a security lens, which has been focused on:
- system names
- vendors
- databases
Those are important, but they don’t get to the heart of privacy risk.
Privacy risk lives in questions like:
- How was this data collected?
- What was the individual told at the point of collection?
- What purposes is the data used for today—not just originally?
- Is that use aligned with expectations?
- Who is the data shared with, and why?
- Has the use changed over time?
If an inventory can’t answer those questions, it won’t support privacy notices, consent decisions, or risk assessments, no matter how complete the system list looks.
Why is a Processing Activity Focus So Important?
When inventories focus only on systems, privacy teams often struggle to:
- keep privacy notices accurate
- evaluate whether consent is required
- explain data use clearly to regulators or customers
- assess whether a use of data is appropriate, even if legal
You can know where data lives and still not understand how it’s being used or whether users were properly informed.
That gap is where privacy risk lives.
A Data Inventory Is a System
I want to be very clear: a data inventory is a system, meaning it’s a repeatable way of capturing, maintaining, and using information about data processing.
That system can absolutely live in a spreadsheet.
I would much rather see:
- a spreadsheet that accurately reflects processing activities and is actively maintained than:
- a sophisticated tool that was implemented once and never fully adopted (and I see a lot of these!)
Tools can help as complexity grows, and if you’re using automated tools to help find data, this is great! If you’re ready for more advanced automation to ensure you know what data is actually in which system, that’s very helpful for efficiency, and there are many tools available to help.
But tools do not perform complete data inventories on their own. Just a few, and definitely not all, of the important questions data inventories help answer:
- Should the data be collected in the first place?
- Exactly HOW is sensitive data collected, used, and shared?
- Was notice properly provided?
- Is the right legal basis or business purpose in place?
- Does data cross borders and is the right cross-border mechanism in place?
What’s the interplay between a Data Map and a Data Inventory?
The technical answer is that a data map is a visual representation of data flowing through a company. A data inventory is detailed documentation about a data process.
Software companies and privacy pros often use them interchangeably.
Some companies have a visual data map showing how data moves from system 1 to system 2. And some companies like taking a data inventory and flipping it also to a visual data map (fun fact, privacy tech can help you do this automatically!)
Do you need both? Not really.
Which do you need? A data inventory is more than a data map. Why? Because the data inventory is what actually explains the legal basis, business purpose, and all the other detailed requirements required under privacy laws.
If you only have a data map, you can still use that to get started and identify the business processes associated with it.
For example, you might show that data moves from the website to SalesForce and within SalesForce it lists name and email (and likely a long list of other data elements, but for our purposes we’re making it super simple). You can ask what business processes are using name and email, such as a new email newsletter signup. Then you can document all the details for email newsletter signup and surveys as separate business processing activities.
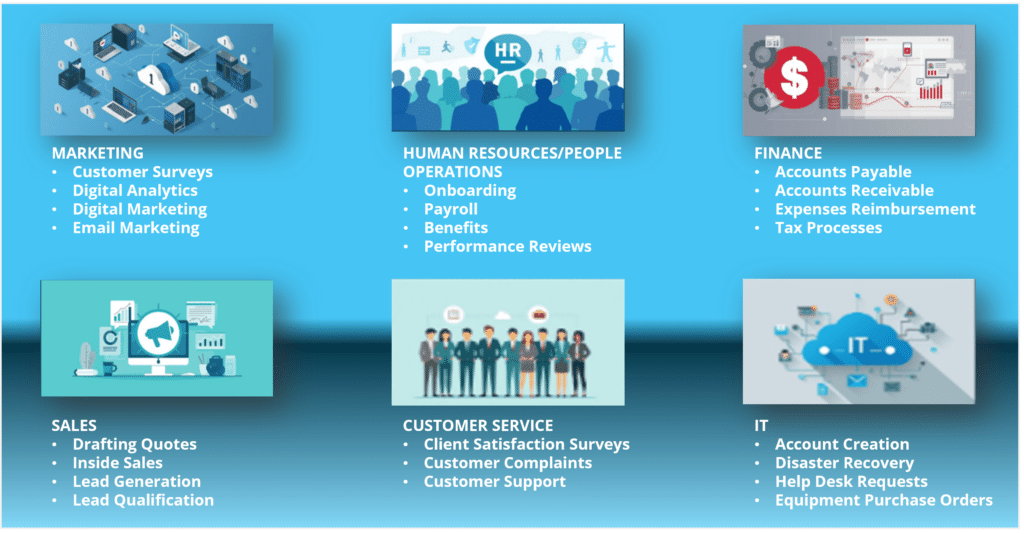
How do I think about processing activities?
Here are some sample activities to help you brainstorm processing activities:
And Yes, There Are Still Deadlines in Year Two (and Beyond)
Another misconception I often hear is that the pressure around data inventories fades after the first year.
In reality, deadlines don’t disappear. They multiply.
They show up as:
- new state laws going into effect
- new vendors
- amendments changing definitions and thresholds
- new product features, launches, and AI initiatives
- using existing data in new ways
- enterprise customer due diligence
- regulator inquiries and enforcement
I haven’t met a company that doesn’t have a business that changes during the year.
What a Useful Privacy Inventory Looks Like
A useful privacy inventory is not the longest or most detailed one.
It’s one that allows a privacy team to confidently answer core questions about:
- what data is collected
- why it’s collected
- how individuals are informed
- where the data goes
- what risks are created
At a minimum, it should support:
- privacy notice accuracy
- consent and opt-out decisions
- privacy rights fulfillment
- vendor oversight
- privacy risk assessments
- AI and new data use reviews
If it can’t do those things, it may exist, but it’s not going to be very useful.
How to Improve an Inventory Without Starting Over
Most companies don’t need to scrap what they have; they need to shift the focus.
The fastest improvements usually come from:
- ensuring a processing activity approach
- prioritizing high-risk processing activities
- documenting how data is collected and used, not just where it lives
- tying inventory updates to real workflows
- validating accuracy on a regular cadence
What should that cadence be?
It depends! Complexity of the business, how often are teams changing vendors and innovating with new products, campaigns, or processes? More often = more regular check-ins. We have some do it quarterly, bi-annually, or annually.
For teams using the assessment or spreadsheet approach, creating a schedule that has regular updates and interviews with teams is essential. If using automation to ensure accuracy with data elements tied to systems, it needs a regular review schedule to flag and review privacy risks.

Need Help?
We talk a LOT about data inventories and have a free spreadsheet, a guide, and we also help companies select the best software for its situation and privacy tech implementations.
There is SO much to talk about data inventories that I can’t possibly do it all in this one newsletter, so stay tuned for more on this topic.
As always, I want this newsletter to reflect what you are navigating right now.
What’s the hardest part of your data inventory today? Getting accuracy, capturing processing activities, keeping it updated, or getting the business to participate?
Hit reply and let me know (I read every response myself), and I’ll include those questions in future issues.
Until next time,
Jodi
💡 When you’re ready, here’s how we can help:
⚙ Privacy Advisory & Implementation: We help companies navigate privacy requirements with confidence. Our advisory support covers strategy, operations, and real-world implementation.
⚙ Fractional Privacy Services: We provide fractional privacy leadership tailored to your needs and pace. From program development to day-to-day support, we help you build and sustain a strong privacy program.

