Oldest children around the world often bond over a specific shared memory.
The parents are gone, they’re in charge, and their younger siblings sneak off to the basement to watch the new, scary movie that just dropped. The normally responsible older sibling doesn’t notice because everyone is quiet and they have some very important things to do.
But after it’s been too quiet for too long, the oldest child knows something is up and finds their siblings clutching each other in fear on a couch downstairs. Knowing they will all get in trouble, the oldest child swears everyone to solemn secrecy.
The whole plan goes off without a hitch. Until later that night around 1 am, that is.
Because at 1 am, the Freddie-Krueger-loving younger siblings wake up the entire house screaming about a nightmare that was definitely caused by watching a show with unfriendly ghosts.
And the oldest child gets grounded for a loooooooong time.
This is a classic example of what privacy consultants call third-party risk management, or TPRM.
In this scenario, the oldest child is the data controller and the younger siblings are data processors. Even though the oldest child didn’t actively do anything wrong, they were the most responsible party involved and therefore bear the brunt of the consequences.
Had they been paying more attention, the older sibling would have realized that more than 20 minutes of total silence never bodes well for babysitters.
It’s basic risk management.
What is TPRM?
TPRM goes by many names—vendor risk management, vendor management, supply chain risk management—but when it comes to privacy, it all means basically the same thing: a strategic risk management program that identifies, prioritizes, and designs processes around potential exposure risks posed by vendors (or contractors, suppliers, partners, etc.) to company-owned customer data.
As evidenced by the constant stream of data breaches in the news over the last two decades, TPRM hasn’t always been a best practice for businesses in any sector. But thanks in large part to regulatory requirements in aggressive new privacy laws, it’s quickly becoming the gold standard.
Why you need a TPRM program right now
If your privacy risk management program is less a comprehensive, cross-functional effort and more an ad hoc, department-by-department type of thing, this post is for you.
First, it’s important to understand the current data privacy landscape. Here’s a basic rundown of the last few years in consumer data privacy.
Early 2010s: Smartphones and apps take over the data collection and analytics scene as companies begin to focus on delivering personalized experiences for their customers. This customization relies heavily on large caches of information collected from users, usually without their knowledge or consent.
Arguments from consumer privacy advocates, present for decades, start to gain traction after massive data breaches at major corporations became commonplace and misuse of user data by social media platforms comes to light.
2016: The European Union passes the General Data Protection Regulation, or GDPR. As the first modern, comprehensive consumer data privacy law, the GDPR creates strict new regulations governing consent and requirements for collecting and processing data from EU residents.
2018: The GDPR becomes enforceable. Following the EU’s lead, other governments begin passing similar legislation. Notably, California becomes the first state in the US to pass a robust consumer privacy law with the passage of the California Consumer Privacy Act.
2019–Now: New best practices for data privacy emerge as it becomes clear that data collection and processing will become increasingly regulated. Laws are passed establishing civil, and in some cases criminal, liability when sensitive consumer information is exposed in a data breach. Consumers begin to expect, even demand, more control over how their data is collected and used.
A key tipping point in the evolution of data privacy standards came when companies started being held accountable for a data record’s entire lifecycle through its system. If consumer data is exposed, it doesn’t matter if the hack happened to the business itself or one of its vendors.
Basically, if you’re collecting data, you own the benefits, the operations risk, and the consequences full-stop.
A TPRM program helps reduce security and compliance risks in your third-party ecosystem, and it also can reduce both the likelihood and the severity of a data breach. From a privacy standpoint, it helps you identify issues like how a vendor might be using company data and help protect against concerns like reputational damage.
A bonus? It can also help improve the security and privacy compliance of a remote workforce, which is essential in the post-pandemic world.
TPRM best practices
Vendor risk management isn’t a new concept. It’s been part of standard operations management for decades. The important role it plays in data privacy may be new, but it shouldn’t be surprising given that over 51% of organizations have experienced a data breach caused by a third party.
The following best practices can be used to build a strong TPRM program.
Establish internal governance
Before implementing a TPRM program, you need to get your own house in order by:
- Figuring out which privacy laws apply to you (there may be more than one)
- Completing a data inventory that explains how you collect, use, and store customer data
- Updating privacy policies and internal processes to establish regulatory compliance and meet best practice standards
- Providing regular, organization-wide employee training on privacy-related issues
- Defining systems requirements and establishing guidelines for vendor procurement
- Creating a thorough incident response plan that includes processes for containment, customer notification, and system repair
Rank your vendors according to risk
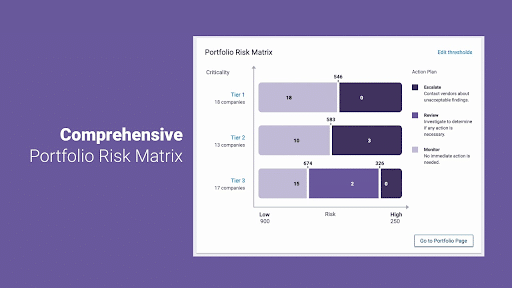
A good TPRM program is less of a to-do list than it is a matrix. It requires balancing how important a vendor is to an organization’s daily operations with the amount—and type—of personal data they process and the amount of exposure risk they provide.
Performing a privacy risk assessment for each vendor can give you critical insight into which vendors are operation-critical and which are high risk. If there is a vendor who ticks both boxes, immediate action is required.
Complete due diligence
Telling a third-party vendor what is expected of them is essential, but making sure they’re following through is even more important.
The SOPs of a strong TPRM program will include regular due diligence checks to ensure best practice standards and contractual obligations are being met. If compliance issues are found, there should be clear steps to remedy the situation.
You don’t need to be the overwhelmed babysitter
Companies trying to build privacy management programs are often like the oldest child babysitter. They know they need to be paying attention, but they’ve got other priorities on their mind.
We can be your co-sitter.
At Red Clover Advisors, we know that privacy isn’t just about compliance. It’s about customers.
Businesses that implement strong, consumer-centric privacy programs realize improvements in customer satisfaction, operational efficiencies, risk reduction, and industry reputation that can outweigh the cost and effort.
Whether you need help managing your third-party risk, training your employees, or understanding your data collection processes, put our passion for privacy to work for you by calling us today.