In a Latrobe, PA drugstore in 1904, apprentice pharmacist David “Doc” Strickler was challenged by a customer at the soda counter to make something “different.” Ice cream sundaes had been part of American cuisine for over a decade, but bananas had only recently become both affordable and widely available.
Looking at the bananas on his counter, the 23-year-old college student sliced the banana in half and topped it with chocolate ice cream covered in chocolate syrup, strawberry ice cream covered in strawberry syrup, and vanilla ice cream covered in pineapple syrup.
In a nod to the ever-popular sundae, he topped the whole thing with whipped cream, nuts, and maraschino cherries.
And the banana split was born.
But how is a banana split like a data privacy program?
We know. Going from the history of one of America’s most famous desserts to data privacy is a big leap. But stick with us and you’ll see what we mean.
Just like a banana split came out of years of incremental improvements in both ice cream making and freezer technologies in general, today’s data privacy landscape is heavily influenced by decades of technological advancements and consumer privacy rights advocacy.
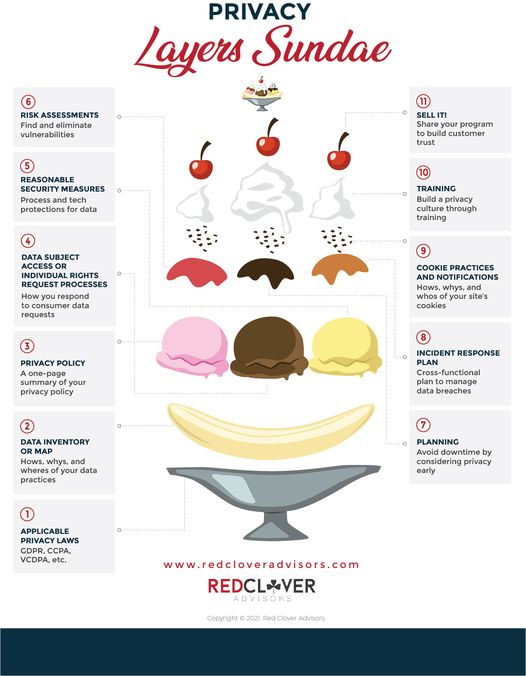
And, just like a banana split has multiple layers that have to be assembled in a certain order, building an efficient, effective data privacy program requires a strong foundation based on methodical, step-by-step processes.
At Red Clover Advisors, we have the secret recipe you need to build a leading privacy program that will change the way your customers, your employees, and your industry view your company.
So put on your apron, grab an ice cream scoop, and let’s get started.
Step 1: Find your dish (or applicable privacy law)
Obviously, one of the things that sets banana splits apart from traditional ice cream sundaes is the inclusion of, well, bananas. Sundaes were usually made in the same funnel-shaped glasses as ice cream sodas, but those glasses weren’t designed to hold bananas (or multiple flavors of ice cream and syrups, for that matter). After the boat-shaped dish we associate with banana splits became common at soda fountains across the country, the ice cream game changed forever.
Just like the banana boat neatly contains the banana halves and catches all those tasty drips, privacy laws like the EU’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) set the parameters for what your privacy program needs to be. (Hint: depending on your business, you might be subject to more than one regulation).
While we recommend building a program that goes beyond compliance and is capable of quickly adapting to regulatory changes, knowing which regulation(s) apply to your business is critical to ensuring you have the right functionalities built in from the beginning.
If you try adding the banana after you’ve scooped the ice cream, poured the syrup, and sprayed the whipped cream, you’ll end up with a mess that only partially resembles a true banana split. If you try to cram this concoction into a bowl that isn’t the right size, you’ll have an even bigger mess. And if you try to cram your existing privacy practices into compliance with data privacy laws retroactively, you’ll get about the same result.
Step 2: Slice your banana (or build your data map)
You can’t have a banana split without a banana, and you can’t build a data privacy program if you don’t know what data you are collecting, why you’re collecting it, who you’re sharing it with, and where you’re storing it.
A data map, also known as a data inventory, gives you all those answers and more. The data inventory process helps you understand exactly what happens to every data record that travels through your system. It also will show you exactly where your data is vulnerable to exposure, which is key to establishing the “reasonable security measures” required by most privacy laws.
Step 3: Scoop your first flavor (or, build your reasonable security measures)
Traditional banana splits have just three ice cream flavors: chocolate, strawberry, and vanilla.
We are going to make the “reasonable security measures” the chocolate scoop because its depth of flavor and decadence anchors the lighter, fruitier flavors, just like your cyber and information security anchors your privacy program.
Under newer privacy laws, companies that don’t take reasonable security measures can be held civilly (even criminally, in some cases) liable if a consumer’s personally identifiable information is exposed in a data breach. Protecting your data with multiple layers of security by checking up on your permission structures, acceptable use policies, internal password and network access practices, and IT protocols for staying on top of updates, patches, and licensing requirements will form the foundation of your breach prevention and response plans.
Step 4: Scoop your second flavor (or establish your data subject access request [DSAR] processes)
Nearly every privacy law requires you to give users a way to easily know about, correct, and delete the sensitive personal information you’ve collected from them. Also known as individual rights requests, a DSAR is how individual consumers execute that right.
DSARs (or individual rights requests) are limited in scope with specific requirements depending on the relevant laws. To achieve compliance, you will need an internal playbook that has been documented, tested, and reviewed, and your team needs to be trained on how to use it in order to respond appropriately to consumers within strict, statutory timelines.
Step 5: Scoop your third flavor (or write your company’s privacy policy)
Too often, companies put out a privacy policy full of what they (or their lawyers) think it should say rather than writing a document that accurately reflects their data privacy practices. Waiting to write the policy until you know what your regulatory obligations are, understanding what happens to your data, having created a thorough infosec plan, and having established your DSAR processes means your privacy policy will match your data collection and use practices.
One more hint: ditch the four pages of dense legalese. Make your policy easy for your customers to understand. They’ll thank you.
Step 6: Pour your first syrup (or complete a risk assessment)
You can never fully eliminate your data’s exposure risk, but a thorough privacy impact assessment will reveal vulnerabilities and significantly reduce a hacker’s windows of opportunity.
Step 7: Pour your second syrup (or test all your systems)
Once you’ve fixed whatever problems were uncovered by the risk assessment, testing your systems and processes before go-live will allow you to troubleshoot problems and avoid downtime so you can continue providing great and safe service to your customers. It’s also important to have regularly scheduled updates to your systems to ensure that all risks are mitigated.
Step 8: Pour your final syrup (or create an incident response plan)
A cross-functional incident response plan with input from all business-critical teams goes a long way in containing and limiting the impact a breach has on your data, reputation, and revenue—and once you have a plan, it’s critical to have it documented, printed, and reviewed or practiced annually.
Adverse events are usually much less adverse if everyone knows what they are supposed to do and trusts that everyone else knows and will complete their jobs too.
Step 9: Sprinkle the cookie crumbles (or evaluate and update your cookie practices and notifications)
Okay, technically this layer is supposed to be chopped nuts. But the pun was too good to skip, so we made it cookie crumbles instead.
To stay current with best practices and comply with current privacy laws, you need to make sure you know what cookies are on your site and what data they are collecting. And thanks to Apple, Google, and Mozilla, you should also be phasing out your third-party cookies. Then you can be confident your cookie banners are up-to-date and launching at the right time.
Step 10: Spray three whipped cream swirls (or training, training, training)
The fact that we’ve given three banana split elements the same part of a data privacy program should tell you how important it is.
Your data privacy program is only as strong as your employees’ understanding of it. Whether it’s five minutes in a staff meeting or a full-day symposium, consistent emphasis on the importance of every action from every employee to data privacy is key to building a company culture that respects and honors customers.
Step 11: Put the cherry on top (or sell it!)
Getting credit from your customers for being a forward-thinking, consumer-focused company is the sweet reward at the end of the long, privacy-program-building road. But you won’t get props if you don’t tell people what you’re doing. Turn your marketing team loose to sell your privacy program as the great value-add it is.
Enjoy a sweet treat
RCA excels at creating privacy-focused data strategy and digital marketing plans. We can help you build your privacy strategy and ensure your ongoing success. Contact us today to get started building your own data privacy banana split.