Let’s talk about vendors.
If you’re reading this page, you probably use them. You know they can expand your business services, streamline your operations, and make you more competitive.
But do you also know that they can also put your business at risk for a data breach and keep you from being compliant with privacy regulations, potentially exposing you to fines and injunctions?
Most businesses have risk management programs in place for operations and financial processes. They may even have one for their reputation.
With new data privacy laws being passed every year, and with consumers increasingly demanding more control over how their sensitive personal information is collected and used, it’s time to add a vendor privacy risk management program.
The Basics of Privacy Risk Management For Vendors
So what does a Vendor Management Guide look like when it comes to privacy?
In technical industry-speak, a vendor risk management program involves any function that falls under the scope of mitigating the risks posed by incorporating third-party vendors into your business operations.
In plain terms, vendor risk management is everything you do to make sure your vendors follow the same standards you do when collecting, processing, and sharing information about your customers.
The goal of a vendor risk management program is to reduce external risks to your data security and privacy practices and to prevent business disruption, compromised data, and financial and reputational damage.
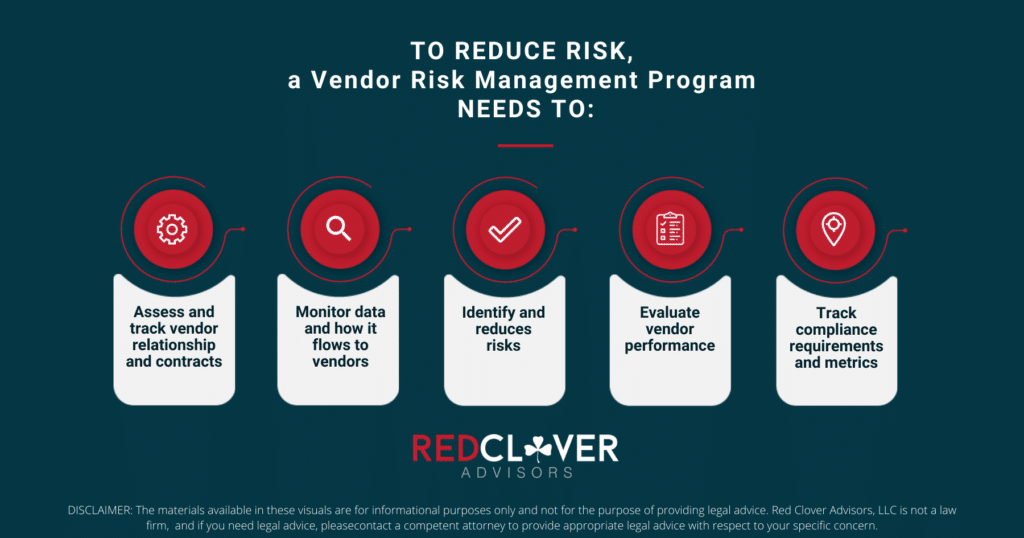
As with any complex, nuanced issue, your program and processes need to be comprehensive. This means you need to be able to:
- Assess and track vendor relationships and contracts
- Monitor data and how it flows to vendors
- Identify and reduce risks
- Evaluate vendor performance
- Track compliance requirements and metrics
Whether this challenge sounds easy-peasy, lemon squeezy or difficult-difficult, lemon difficult, knowing how your third-party vendors treat your data and your customers’ data is critical to helping you win the privacy compliance game.
Who Qualifies as a Vendor?
Vendors don’t fit neatly into one little box, and neither do vendor relationships because the definition of “vendor” varies by regulatory framework.
The California Consumer Privacy Act (CCPA) views vendors differently than the General Data Protection Regulation does. (Even terminology is different – under GDPR, vendors are known as “processors” while CCPA calls them “service providers.”)
For the purposes of this guide, the term “vendor” encompasses a huge variety of relationships, services, and agreements. These relationships can:
- Be short or long-term relationships
- Involve formal contracts or verbal agreements
- Be paid or unpaid
- Be with small mom-and-pop outfits, independent contractors, multinational companies, and more
Vendors don’t just provide IT or software services, either. When we’re talking about data privacy, security, and compliance, any past, present, or future business arrangement between an organization and another entity, by contract or otherwise, can qualify as a vendor. Here are a few examples:
- The IT provider who maintains your company-wide servers
- The marketing agency that manages your email marketing campaigns
- The HR provider who helps you run your payroll services
- The Software-as-a-Service (SaaS) provider who offers a free trial of a customer management solution
Whether you do it or you delegate the job to someone else, you need to establish processes for overseeing everything about your relationship with all types of vendors.
How Do Vendors Impact Data Security and Privacy?
Before we dive into how to build a solid Vendor Management Guide, let’s take a look at why it’s so critical to have these processes in the first place. Knowing what’s really at stake helps you address vendors and extend your data privacy obligations along your entire supply chain.
Vendors can pose:
- Operational risks (a breach or injunction that paralyzes your system)
- Data security risks (a hack that exposes your customers’ data)
- Financial risks (from regulatory fines and lost business)
- Legal and regulatory risks (civil and criminal liability)
- Reputational risks (loss of consumer trust)
Unfortunately, these risks can have a cascading effect, with failure in one area leading to failure in another. That’s why vendor evaluation should be taken seriously from start to finish. (And beyond.)

How to Build Your Vendor Management Guide
A good Vendor Management Guide should reflect how much security your data demands, how risk tolerant your organization is, and the degree of risk associated with how the vendor is handling your data. For optimal results, your program should start before your vendors are even onboarded.
Developing a vendor privacy risk management program should follow these steps:
- Identify your vendors
- Assign a risk category (critical, high, medium, low) to each existing vendor
- Vet new vendors
- Continually review and manage your program

Identify Your Vendors and the Scope of Your Relationship
Do you know who all your vendors are? You probably have a list, but does that list account for everyone you have a vendor relationship with?
If you’ve already completed a data inventory, then the answer is probably yes. If you haven’t mapped your data yet, stop reading this guide and start mapping your data right now.
Your vendor master list should contain all critical vendor information, including the who, what, when, where, and why of each relationship. But here’s the kicker: your list also needs to include your vendors’ vendors, also known as subprocessors.
Why are subprocessors important?
Via your third-party vendor, subprocessors often end up with access to your data—and your clients’ data. If they have security issues, you have security issues, plain and simple.
Know the Risks
Not all risk is created equal. In fact, some level of risk is unavoidable.
The goal of a vendor privacy risk management program isn’t to avoid all risk but rather to understand exactly what the risks are and build appropriate internal controls to manage them.
Some of your vendors may not have access to sensitive information. Some may already enforce strict privacy processes. Some may be a disaster. Assigning a risk level to each vendor will help you know which vendors present the biggest risk to your business and which processes need mitigating first.
- Critical risk: These vendors are mission-critical to your business operations. If they can’t deliver the contracted services, it could shut everything down.
- High risk: These vendors either have access to customer data and there is a high risk of information loss or are relied upon by your organization to a high degree.
- Medium risk: These vendors have limited access to customer information, but losing them would still be disruptive to your business operations.
- Low risk: These vendors don’t have access to customer data and don’t have a daily impact on your business operations.
Vet New Vendors
Regardless of whether you need a new vendor because your old vendor isn’t secure enough or because you need new functionalities, new vendors must be carefully vetted.
Vetting doesn’t mean doing a Google search or reading reviews on LinkedIn. A thorough vetting process involves following a standardized checklist for each and every potential vendor. Obviously, you should get references. But your critical and high-risk vendors should also provide you with:
- Evidence of their information security policies, disaster recovery test results, proof of insurance, etc.
- Evidence of their ability to ensure continuity of service
- Evidence their incident management program meets industry compliance and best practice standards
- Standards for their internal documenting and reporting procedures
If a request for this information is not welcomed by the vendor, they’ve reached the “Stop, Do Not Pass Go” on your privacy game board.
Review and Manage Your Program
Privacy and compliance is an ongoing journey, not a one-and-done thing. To be truly effective, your vendor privacy risk management program needs to be able to handle onboarding new vendors, troubleshooting existing partnerships, terminating contracts, and everything in between.
Besides a data inventory, your program should also involve regular vendor assessments. The privacy industry gold standard best practice is to require that your vendors regularly self-audit their privacy and security practices through a questionnaire that should, at the minimum, cover your vendors’:
- Business relationships
- Data handling and security practices
- Incident management and response plans
- Reasons for and scope of data usage
- Data usage and storage plans
- Cross-border requirements
- Individual rights capabilities
- Privacy notice disclosures
These questionnaires should be sent annually to help you monitor vendors, track new risks, and prevent security threats from reaching your business and your customers.
Vendor performance management
Privacy and data security are key, but let’s pause for a moment to look at performance management. Are your vendors meeting your expectations and established milestones as well as living up to your service-level agreements and KPIs?
Working with your team
Does everyone in your organization understand the potential risks that vendors pose? When it comes to data security and privacy, you should be investing in team training. It’s a best practice, but may also be required. The prevalence of free vendors can be a weak link for your team and a solid privacy training program can bring everyone onto the same page.
Compliance Requirements for Your Contracts
So, now that you know why you need a vendor privacy risk management program and how to build one, let’s talk contracts. Cross-departmental contract review processes involving legal, procurement, and leadership teams should be part of your vendor privacy risk management program. As with your privacy and security questionnaires, your contracts should be reviewed annually.
Existing privacy laws have basic requirements for vendor contracts involving the collection and processing of consumer data. These compliance requirements should be both in your contracts and part of your vendor risk management program and should establish a mutually beneficial, mutually protected relationship by:
- Making provisions for the cross-border transfer of data
- Defining terms and related parameters with regards to data protection
- Including guidelines for the confidentiality and accessibility to data
- Establishing end-of-contract obligations

Cross-border data transfers
We know that data has a serious case of wanderlust. It can move from vendor to vendor in the blink of an eye. And before you know it, it’s made its way over to the EU. (Or vice versa.)
When data travels like this, it’s called a cross-border transfer. Your contract should include provisions for how your vendor manages this process and what steps they have in place to manage the specific requirements that might be triggered by new jurisdictions. This could take the form of something known as Standard Contractual Clauses (or “SCCs”) between you and your vendor on opposite sides of the Atlantic. Note: in June 2021, new changes were announced to the SCC. These changes will apply to new SCCs, and will also need to be implemented for existing SCCs and be phased in over time.
Data protection addendums
Your contract must define personal data and sensitive information in the context of your working relationship. Who are the data owners, and who is the third party in your written agreement? Can the data be used for other purposes, or by businesses who aren’t direct service providers or processors? Establishing this on the front end helps you both understand how you’ll work together.
You’ll also need to define the purpose and duration of the agreement and make sure the vendor certifies that it understands the provisions of the contract. It needs to be clear what you’re asking them to comply with regarding privacy program management and risk mitigation.
Confidentiality & accessibility
Your contract needs to put forth what data is being collected and who has access to it. It should ensure that each person processing personal data is subject to the duty of confidentiality.
The overarching goal should be to ensure strict limitations to accessibility and minimize what personal data is disclosed.
Audits & support
Your contract should cover any requirements for audits and support needed to conduct data privacy assessments. Much like minimizing data disclosure, your contract should strive to include only strictly necessary measures for audits.
Your contract should also require that subprocessors adhere to the same privacy and security obligations as those of the vendor and detail what kind of help your vendors will provide for fulfilling individual rights requests and in cases of data breaches.
End-of-contract obligations
No vendor relationship lasts forever. Your contract needs to spell out what happens to data when you part ways. Do they return it? Destroy it? What about subprocessors? Make sure to be thorough here to protect your customers.
Contract Requirements by State
So far, California, Virginia, and Colorado are the only states that have passed data privacy laws with rules on vendor contracts, but other states either are in the process of writing new laws or will be soon.
Here’s what those rules look like by state.
California
The California Consumer Privacy Act (CCPA) and the soon-to-be-enacted California Privacy Regulation Act (CPRA) are the strictest US privacy laws currently in place.
These regulations state that a business that collects a consumer’s personal information and sells it to or shares it with a third party or discloses it to a service provider or contractor for a business purpose is required to enter into an agreement with the third party, service provider or contractor that includes specific listed terms prohibiting:
- Selling or sharing personal information.
- Using personal information for any purpose other than for the business purpose specified in the contract.
- Using personal information outside of the direct business relationship.
- Combining the personal information with other personal information, subject to certain exceptions.
Vendor contracts also must include a certification that contractors understand these restrictions, and the vendee must be permitted to monitor compliance.
Virginia
The Virginia Consumer Data Protection Act (VCDPA) goes into effect January 1, 2023, and requires vendor contracts that involve the collection or processing of consumer data to include the following provisions:
- Each person processing personal data is subject to a duty of confidentiality.
- At the controller’s direction, vendors must delete or return all personal data to the controller as requested after providing services, unless retention is required by law.
- Vendors must make available to the controller, at its request, all information in its possession necessary to demonstrate the processor’s compliance with the obligations in the CDPA.
- Vendors must allow and cooperate with reasonable assessments by the controller or arrange for a qualified and independent assessor to conduct an assessment of the processor’s policies and technical and organizational measures, providing a report of such assessment to the controller upon request.
- If vendors engage any subcontractor pursuant to a written contract, the subcontractor must also meet the obligations of the processor with respect to the personal data.
Colorado
The recently passed Colorado Privacy Act (CPA) stipulates that processors are required to adhere to the instructions of the controller and assist the controller in meeting its obligations by:
- Taking appropriate measures to assist the controller in responding to consumer requests to exercise their rights
- Helping meet the controller’s security obligations in relation to breach notification and system security
- Providing necessary information to the controller to enable the controller to conduct and document any data protection assessments required.
Additionally, processing by a processor must be governed by a binding contract between the processor and controller that sets out:
- Instructions, including the nature and purpose of the processing, to which the processor is bound.
- The duration of processing and the type of personal data subject to the processing.
- The requirement that each person processing the personal data is subject to a duty of confidentiality with respect to the data.
- The requirement that a controller may only use a subcontractor pursuant to a contract requiring the subcontractor to meet the processor’s obligations with respect to the data. The processor must also provide the controller with an opportunity to object.
- The allocation of responsibility between the controller and processor for maintaining technical and organizational and technical measures to ensure appropriate security.
- Whether the controller requires the processor to return or delete all personal data to the controller at the end of the provision of services unless that retention is required by law.
- That the processor shall make all information necessary to demonstrate compliance with this law available to the controller
- The processor shall allow for, and contribute to, reasonable audits and inspections by the controller or auditor.
Third-Party Risk Management Guide
Check out our Third-Party Risk Management Guide for tips and practical guidance you can implement right away.
Get the Expert Help You Need
Moving forward into the new, privacy-centric business world, vendors pose a substantial risk to any company.
Whether you’re five days into a vendor relationship or five years, whether your state has passed a privacy law or not, you need to follow privacy best practices to protect yourself and your clients.
Red Clover Advisors has been making data privacy practices simple and straightforward for clients since our first day. Whether you’re a fresh startup that wants to prioritize privacy and compliance training from the get-go to an established business needing to reshape your approach, our approach provides your team with information that is practical and actionable.
Take your company beyond compliance. Reach out to our team at Red Clover Advisors today to start with your free consultation.


