COVID-19 has distributed a wave of anxiety across the world.
Worry of getting sick in addition to economic meltdown has people on every continent shivering with fear. And as if that wasn’t enough, some people see the pandemic as an opportunity to exploit this fear for financial gain.
One way they’re doing this is through emails that trick you into spending your money or providing sensitive information.
We call these phishing scams.
In fact, Google reports a 350% increase in the creation of phishing websites since the pandemic started in 2020.
Because almost everyone is working remotely at this time, phishing scams are easier to pull off. After all, home cyber security is almost never as beefed up as a company workplace. When you consider the speed at which the world transitioned from the office to a home work environment, there really wasn’t any time to set up cybersecurity for personal computers.
Add in the fact that almost all children are now finishing the year’s educational tasks on personal devices, and phishing scams have a world of opportunity in front of them.
With that in mind, we’re revealing how to identify a phishing scam and how to protect yourself proactively against being a target.
What is a Phishing Email?
Phishing scams are the most popular type of cybercrimes, making up for 90% of data breaches in 2019.
The successful attacks have resulted in billions of dollars lost to scammers – $26 billion in the past four years, to be exact. But how do people fall for these scams?
It’s simple really… they were tricked.
A phishing email – sometimes also referred to as business email compromise – is a targeted email in which a cyber criminal sends an email that appears to be from a legitimate company or person. This message asks the recipient to click a disguised malware link or provide sensitive information.
Imagine you just received an email from your company’s “CEO” stating he’s on a business trip and needs you to provide him the company credit card information.
You might not think twice… he is the CEO after all.
But what you may not know is it’s very easy for a scammer to disguise himself or herself as someone else via email. This is a common example of a phishing email.
Who Do Phishing Emails Target?
Who phishing emails target really depends on the cybercriminals behind the computer. Sometimes they’re attempting to go after an individual and sometimes they’re trying to go after an entire organization.
Attacks on Individuals
When attacking individuals, scammers might pose as a business you actively use or trust. For example, a store you frequently shop at, a social network, or a bank. They might even pretend to be someone you know.
Attacks on Businesses
Phishing emails are one of the most common attacks on businesses with 76% of businesses reporting they were victims of phishing attacks in 2019.
And don’t think because you’re a small company they won’t come after you: 43% of all phishing scams target small businesses.
For example, hackers will send an email asking masking themselves as an employer that needs you to wire money to them. Another common occurrence is a malware link: An email contains an innocent-looking URL that actually installs destructive malware that gives hackers access to your devices.
SMS, apps, and networks are other ways hackers can attack via the internet.
To get a head start on protecting your business, implement cybersecurity best practices for small businesses. You can also protect your business by understanding the hacker’s playbook. Cybercriminals execute their phishing emails with a four-step process:
Identify a Target
First, cybercriminals will choose their victims. Typically, this is someone in your organization who’s close to the money. This might be someone in accounting or the financial department. They’ll find this person by doing some research about your company, its employees and its executives.
Groom the Target
Next, the cybercriminal will write up and send an email addressed from a customer or an executive of the company. The email will always have some type of urgent call to action.
Exchange Information
The victim will receive the scam email. But naturally, they’ll be deceived and begin executing upon the call to action believing they’re conducting a legitimate business transaction.
Hack Completed
Once the transaction is complete, it’s too late. If a link was clicked or money was transferred, the scammer has won.
How to Identify a Phishing Email During COVID-19
Why? Because when people are afraid, they’re more vulnerable.
Today, a phishing email targeted COVID-19 information such as places to get medical equipment like masks or free technology to stay in touch with friends and family remotely.
So, how do you identify a phishing email before you make an irreversible and damaging mistake?
There are advising services and even a slew of software options available to help stop scams before they happen. But training yourself and your employees to spot phishing emails is an easy place to start.
The Red Flags
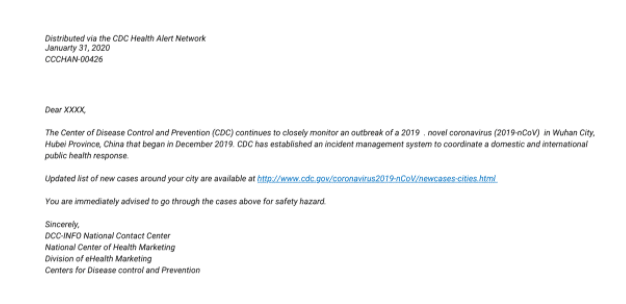
During COVID-19, you or someone in your company might receive a phishing email that appears to be from the CDC or a credible health organization. And it will likely prompt you to take urgent action by clicking a link or downloading a file.
Let’s take a look at an example.
This looks like a legitimate email. But there are a couple red flags you can notice almost immediately. Here are a few red flags that might indicate you received a phishing email:
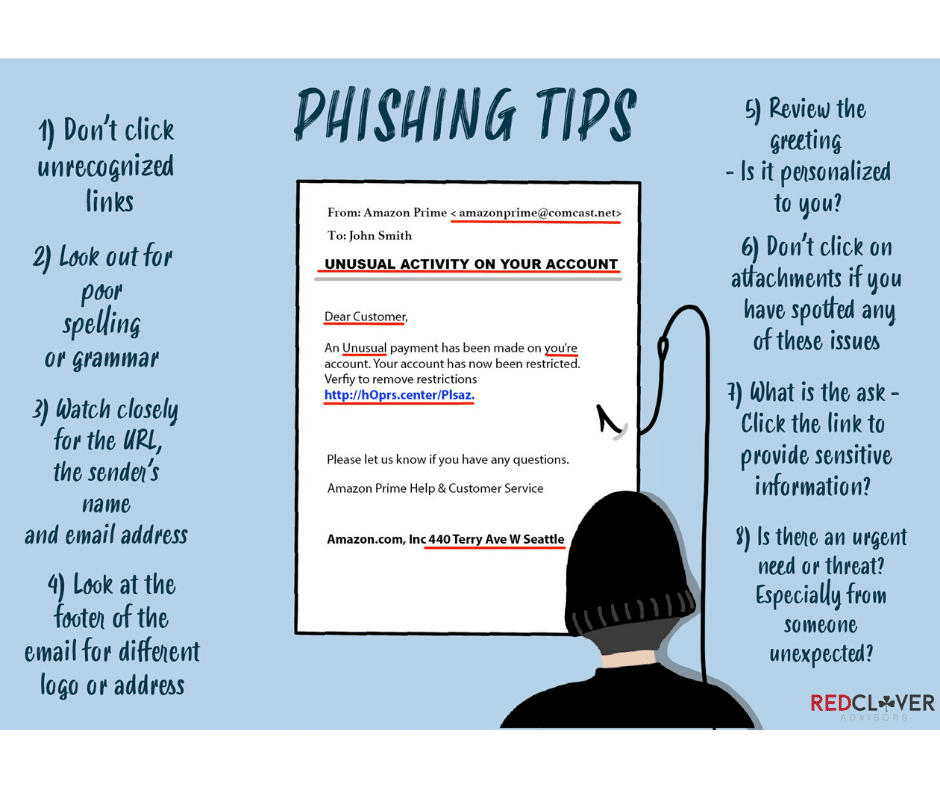
Poor Grammar
Attackers often live in different countries than the people they’re scamming. For this reason, there will often be some type of language barrier in the form of spelling and grammatical errors.
Check the Introduction
A legitimate business will address you by your name, especially if it’s asking you to take action on an account. Informal or impersonal salutations are a major red flag.
Urgent Call to Action
If the email instills a bit of panic, that’s a red flag. Keep an eye out for terms such as immediate or urgent. In the email example above, the line “you are immediately advised to go through the cases above for safety hazard” is a huge no-no. The hacker is setting up a sense of urgency in hopes the end user will click the malware link.
Verifying a Phishing Email
Once you’ve identified a red flag, how do you verify you have in fact received a phishing email? There are a couple of ways.
Call the sender
Whether it’s the “CDC” or your “CEO” who sent the email, give them a call. They’ll be able to verify whether the email is legitimate before you click a link or send back any sensitive information. Better to be safe than sorry!
You’re asked for personal information
A coronavirus-themed email that asks you for any kind of personal information is a phishing scam. A government agency will never ask for that kind of information over email. Never respond to an email and include your personal information.
Check the email address or link
You can inspect a link without clicking it. Simply hover over the hyperlink with your mouse and see to what it actually links. If it isn’t from the proposed sender, delete the email immediately.
To check the email address, click on the sender’s email address. If it’s not an email address from the proposed sender (xxx@cdc.com) delete the email. Beware of any email that says it’s from the CDC but when you check it, it’s actually from a generic email such as yahoo.com or gmail.com. And don’t trust emails from the government with links ending in .org instead of .gov.
Protecting Yourself from Phishing Emails
Usually, red flags and simple checking methods can expose a phishing email. But not always. Sometimes a phishing email is so well crafted even the most trained IT professionals can be deceived.
It’s always best to protect yourself. Here are a few ways to do just that:
Email Filters
Email filters alone won’t keep the phishing emails away for good. But it will definitely help. Some email providers have more effective spam filters than others, so choose your email provider wisely.
Antivirus Softwares
Antivirus softwares will protect you from all kinds of dangerous cyberthreats. Make sure you regularly scan your device and keep the software updated.
VPNs
Virtual Private Networks (VPNs) help to maintain security while online, particularly when using a public WiFi connection. Download this guide for a list of suggested VPNs to use.
Educate yourself and your employees
Training is critical to identifying phishing emails. Run simulated phishing tests and let people know if they passed or failed. This will allow you to be confident everyone in your office is aware of the risks.
Conclusion: Always Go to the Source
Keep in mind it’s extremely unlikely the CDC or World Health Organization will personally send you an email. And understand that at a time like this, ne’er-do-wells are taking advantage of the fact that fear and stress is at an all time high and attention to things like cybersecurity is not top of mind.
Anyone who’s looking to steal money or gain access to confidential information is going to try to do so at this time when your guard is down. Knowing these things, it’s imperative to be on alert. If you think you might have received a phishing email, it’s always best to go directly to the source.
Here are a few of the best resources to follow to get the most updated information about the COVID-19 outbreak:
If you’re interested in setting up security measures for your business, contact us today for a complimentary consultation.